
Credential Theft via Direct Poisoned Pipeline Execution (Direct-PPE) Attacks on AWS, Azure, and GCP
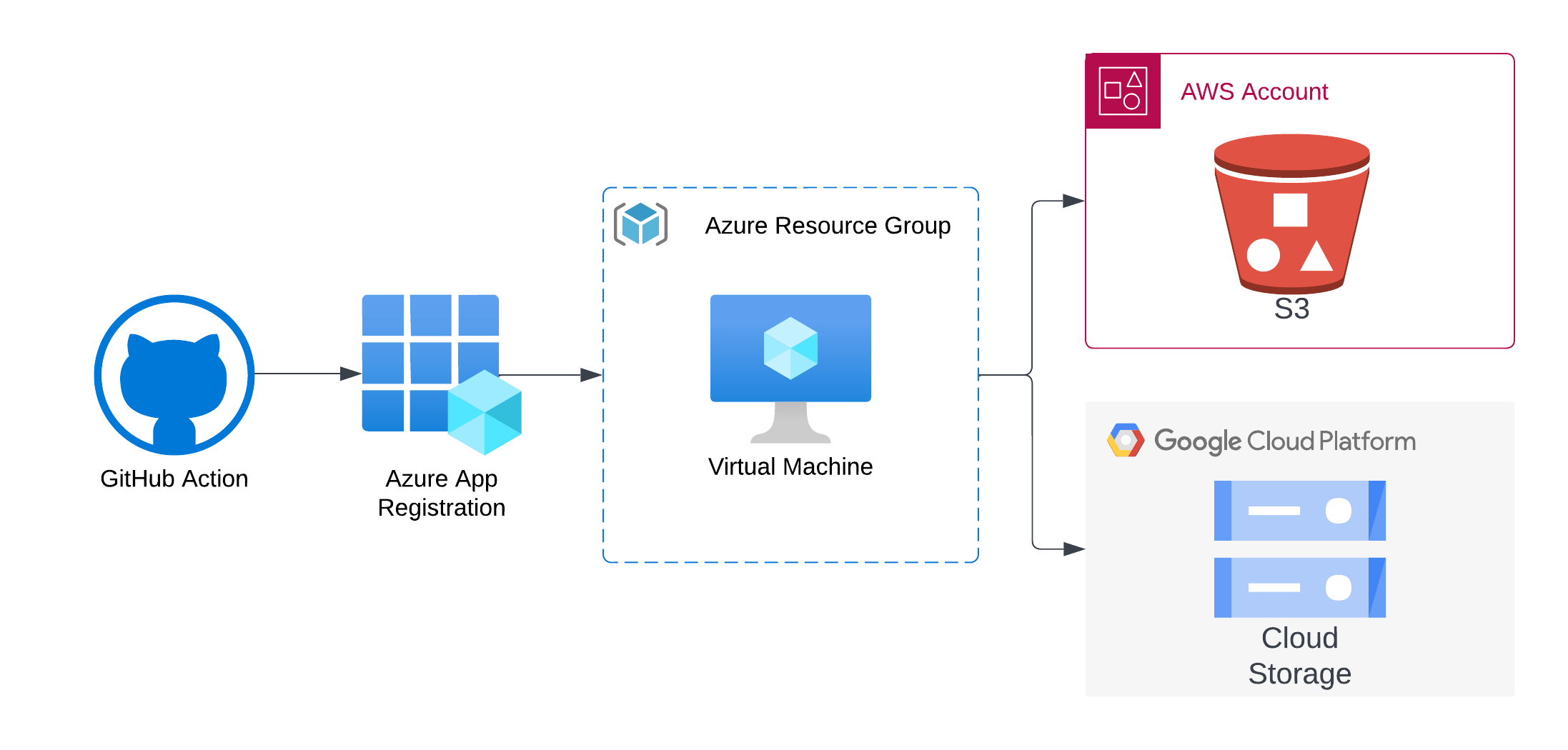
Credential Theft via Direct Poisoned Pipeline Execution (Direct-PPE) Attacks on AWS, Azure, and GCP In this short blog post, I’ll show how an attacker with existing access to a source code management (SCM) system can abuse malicious pipeline configurations to steal cloud tokens and escalate access across AWS, Azure, or GCP environments. Direct-PPE First, let’s clarify what Direct Poisoned Pipeline Execution (Direct-PPE) means and outline the breach scenario we’ll use to demonstrate how attackers can leverage it to further compromise cloud environments like AWS, Azure, and GCP. ...
Authentication in the Cloud
Introduction I’ve noticed that many people in our field, even in 2025, still authenticate themselves and machines using old-fashioned way, such as passwords or long-term credentials. This short blog post takes elements from various resources to emphasize the importance of short-lived credentials for both humans and machines. The main focus of this blog is to promote the use of FIDO for user authentication and OIDC for machine authentication to avoid relying on long-term credentials. ...
Azure NSM
Introduction In today’s dynamic cloud environments, detecting and mitigating network scans is crucial for ensuring the security and health of your infrastructure. Azure provides robust tools like VNet Flow Logs, Log Analytics, and custom KQL (Kusto Query Language) rules that can help you detect and respond to both horizontal and vertical network scans. In this post, we will dive into how you can leverage these tools to build effective detection mechanisms for network scans in Azure. We will cover key concepts like VNet flow logs, network architecture best practices, and provide step-by-step guidance on creating custom KQL queries to identify scanning activities in your environment. Whether you’re an Azure security enthusiast or a network administrator, this guide will empower you to enhance your cloud network monitoring.. ...
Abuse GitHub notifications for phishing
Introduction This morning, I received a phishing notification disguised as a GitHub alert. In this short blog post, I want to share the techniques the attackers used and explain why it can be difficult to recognize such phishing attempts. Email In the image above, the first thing that caught my eye was the random name u7Fbclark, which made me stop before clicking the URL. Firstly, I checked the SPF and DKIM records to ensure that the email was coming from GitHub, and it was indeed from them. In the image below, you can see that both SPF and DKIM checks passed. ...
AWS security baseline architecture
AWS security baseline architecture Introduction Hi there in this blog post, we will talk about AWS cloud security architecture from a thousand-foot View. This blog post is meant for absolute beginners in the cloud security journey. We will discuss how we can achieve perfect isolation of resources and collaboration with each other by following best practices and recommended guides. AWS offers numerous security-related resources, including posts, whitepapers, and guides, as well as two major frameworks: the Cloud Adoption Framework (CAF) and the Well-Architected Framework. However, the abundance of information can make AWS security seem complex and confusing for beginners like myself, and possibly like you. It’s likely that AWS developed the AWS Security Reference Architecture (AWS SRA) in response to this confusion. As its name suggests, the SRA organizes best practices, whitepapers, and guidelines into a cohesive framework, making them easier to follow and implement. According to Amazon, the SRA provides a holistic set of guidelines for deploying AWS security services in a multi-account environment. Before diving into the details of the SRA, let’s first understand why a multi-account strategy is necessary and why prioritizing security services matters. ...